Information security is one of the most important and most popular topics in IT today. Due to the recent shift in work habits and desires, organizations need to improve their IT systems and integrate new solutions that enable safe remote work for employees. At the same time, the costs associated with preparing defenses against cybercrimes are rapidly increasing, from US$7 trillion in 20131 to an estimated US$6 trillion in 2023.2 The challenge for managers is to determine how much to invest in information security.
For those setting an information security budget, determining the amount of money to spend is often a conundrum. It is hard to justify paying for a service that does not generate any revenue and tends to restrict many organization and employee actions. There are three common approaches: the compliance-first approach, the industry-average approach and the naïve approach.
Some organizations take a compliance-first approach because it is much easier to defend a budget that includes requirements for regulatory compliance. Some organizations prefer to look at what other organizations are doing and follow their lead. This can result in recommendations to spend the amount considered average for their industry, or to match the spending of their closest competitors. A third approach is to use the previous year’s budget as the basis for crafting the next year’s budget, but for many reasons, that approach can be naïve.
The best and the worst scenarios for information security both arise when nothing happens.
The problem underlying the decision of which approach to take is that it is difficult for security experts to prove the efficacy of their approach. The best and the worst scenarios for information security both arise when nothing happens. It is a foregone conclusion that an organization’s IT systems will be tested. If there are no detected events, that means either the organization has an exceptionally good security system and all attacks were defended, or that an attack occurred but no one noticed. In today’s IT environment, any device connected to the Internet will, at least, be tested for known vulnerabilities.
It is for this reason that organizations already make investments in cybersecurity defense controls that are either preventive, detective or corrective while simultaneously maintaining administrative, technical or procedural controls that focus on risk mitigation in case a threat makes it through the defense. For example, an organization may invest in a firewall as a preventive technical measures and conduct backups as a necessary corrective technical measure in case the firewall fails. This approach helps maximize the investment return by providing both defensive and corrective actions that mitigate the overall cost of a cybersecurity attack.
Therefore, the current budgeting approaches often focus on investing in a multitude of cybersecurity measures that are difficult to defend during budget discussions. Instead, a risk-first approach to developing and defending an information security budget by evaluating the risk associated with each information security threat is proposed. Information security managers can use this risk-first approach to make informed decisions based on where the organization’s greatest risk lies.
Issues With Current Information Security Budgeting Techniques
As noted, there are challenges and concerns with the current three commonly used approaches to making difficult budget decisions.
Compliance-Based Approach
The privilege of holding customer information comes with the responsibility to protect it. Many countries and jurisdictions have implemented rules about the safe handling of customer data. One method of determining how much to spend on information security is to meet the required standards of relevant governing bodies. This approach is easily defensible in most boardrooms, but it only addresses the organizational costs based on the loss of customer information. Adopting a compliance-first budget often ignores the costs associated with disrupted organizational business processes. This approach focuses on defending against cybercrimes but does not address the administrative actions that can be taken to recover from such an attack. A compliance-based approach does not include an evaluation of all cyberrisk and recovery measures and, therefore, can expose organizations to many future costs.

Industry-Average Approach
The concept of being average makes sense for an organization that is willing to accept the same level of risk that others in the same industry encounter. This approach is reasonably defensible at budget meetings since the critical decision often turns on whether to base spending on a percentage of the IT budget, an average percentage of revenue, or an amount per full-time-equivalent employee. In a study by Deloitte, enterprises spent an average of 10.9 percent of their IT budget on information security in 2020.3 Industry details for percentage of IT budget, percentage of revenue and per full-time employee are provided in figure 1.4
Budgeting aligned with the industry average has three potential flaws. First, spending what others in the industry are spending means the organization will encounter the average number of information security issues as well. Fifty percent will have fewer information security issues and 50 percent will encounter more. This approach, in essence, outsources the decision of how much risk the organization is willing to accept. By default, the organization is accepting the risk associated with the industry. This approach removes the option for an organization to choose to make information security a competitive advantage.
The second flaw is connected to the rising increase in information security spending. Global spending on information security has grown from US$34 billion in 2017 to approximately US$60 billion in 2021.5 This is an increase of 76 percent in four years. Being average means continually trying to spend what others are spending-an approach that may not be sustainable. Organizations must find ways to manage information security costs while minimizing organizational risk.

The final flaw with this approach is associated with how the organization will spend the allocated budget. Figure 2 shows that organizations have not significantly altered the areas associated with spending over the past several years.6 However, this may be due to the third common approach to setting information security budgets, which is the naïve approach.
Naïve Approach
The naïve approach to forecasting is to assume that the future will look like the past-that is, deciding that next year’s information security budget should be the same as the previous year’s budget and the money should be allocated in the same way as in the past. Figure 2 illustrates this approach. The percentages of the IT budget spent in each category remained relatively the same from 2018 to 2020, although information security threats certainly changed. This approach to budgeting may be the easiest to defend, but it is potentially the most flawed since it does not focus on the current risk to the organization.
Implementing a Risk-First Approach
The central focus of information security is to maintain the confidentiality, integrity and availability of an organization’s information. However, there are many actors who seek to change, destroy or steal this information for profit or notoriety, which presents a risk. Taking a risk-first approach to information security starts with the assumption that risk abounds in the information sector, and organizations must find ways to manage this risk.
The insurance industry has taken this approach for decades. Insurance premiums are determined based on the probability of an event occurring and the anticipated financial loss. From an insurance perspective, the expected annual cost of an information security system could be determined by multiplying the projected maximum loss (PML) that would occur if an information attack were successful, multiplied by the probability of the event occurring over the next 12 months:
Expected annual cost = PML x Probability of occurrence
The PML, in insurance terms, is the largest loss the insurance company would expect to pay if the event were to happen.
Using this approach, information security becomes a function of minimizing the financial risk for an organization. This is accomplished by minimizing the likelihood an event will happen while simultaneously trying to find ways to reduce the loss if the event should occur.
Step 1: Estimating the Potential Loss for the Organization
The first task for information security managers is to determine the current expected annual cost of an information security failure. Successful information security attacks often result in both liability and operational costs. Liability costs are associated with data exfiltration (the release of customer data to those who should not have it), and data exfiltration costs include the loss of goodwill, loss of future business and customer data repair costs. On the other hand, operational costs come from disruptions to IT and business processes. Organizations should determine each of these costs for their specific circumstances. To help with this task, figure 3 provides estimates based on professionals surveyed by Ponemon Institute in 2021.7

One observation from this survey is that there is considerable variability in the estimates. The maximum loss estimates for both data exfiltration and business disruption costs range from less than US$10 million to more than US$500 million. Variations could be due to organization size, industry or respondents’ personality attributes. Regardless, the estimates show that significant costs are associated with a loss of information security. To complete this first step, each organization needs to identify the cost that is most appropriate for both data exfiltration and business disruption.
Step 2: Estimating the Probability of a Successful Information Security Attack
This step is likely to depend on the organization’s industry. To help organizations get started, figure 4 shows the percent likelihood of a data exfiltration and business disruption due to a malware attack.8
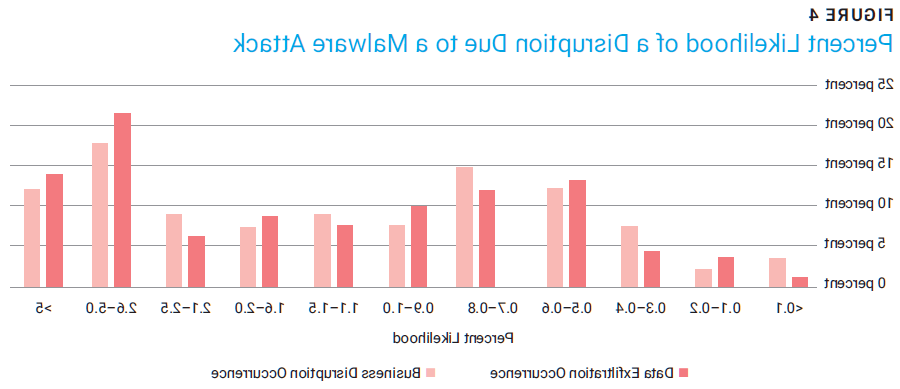
Figure 4 shows that 38 percent of the organizations surveyed estimated the likelihood of an information security attack causing a business disruption to be greater than 2 percent. Similarly, 41 percent estimated the likelihood of a data exfiltration occurrence to be greater than 2 percent. Each organization should use these and other relevant data to help determine the likelihood (by percent) of a disruption due to a successful information security attack. Again, figure 3 is only for a malware attack, so the likelihood of any successful information security attack will be greater than reported in this study.
Step 3: Estimating the Annual Cost of Information Security Attacks
Taking a risk-first approach includes estimating the annual costs associated with information security attacks. This is accomplished by multiplying the PML (step 1) by the estimated likelihood of an occurrence (step 2) for both data exfiltration and business disruption. The following equation can be used to calculate the annual total estimated cost (TEC) of information security attacks:
TEC = (PMLDE x ELDE) + (PMLBD x ELBD)
(Note: DE = data exfiltration; BD = business disruption; EL = Estimated likelihood of an occurrence)

Figure 5 contains the average data in the survey by Ponemon Institute9 and serves as an example of the total estimated cost due to malware.
TEC = (PMLDE x ELDE) + (PMLBD x ELBD) = (US$137.2M x .023) + (US$117.3 x .021) = US$5.6M
The US$5.6 million estimate can serve as a reasonable starting point for many organizations. It does not suggest this is the amount any one organization paid last year. Instead, it represents the current risk for organizations. This is what an insurance company might charge to cover the average risk of covering each of the surveyed 591 clients. Organizations should develop their own PML and estimated likelihoods for business disruptions and data exfiltration and then use these three steps to determine their current 12-month risk.
Step 4: Determining the Estimated Likelihood of an Attack
The projected annual cost of US$5.6 million may come as quite a shock for many IS managers. The natural response might be to either lower the estimated probability of an attack or to reduce the PML. As one article stated, the "problem is that humans are poor at predicting the consequences of their actions or the risk those actions entail due to certain cognitive biases."10 In addition, using a second method can help validate the forecasted costs.
A more scientific approach to estimating the likelihood of an event is to look at the event as a combination of probabilities. For instance, the likelihood of a successful information security attack is influenced by a combination of many failures along the way. A simplified information security system will likely have a firewall that prevents many phishing attacks from getting through. For those attacks that make it through the firewall, many more will be stopped by the antimalware software in place. A small percentage will reach the inbox of an employee who should be trained to not open suspicious emails or provide information.
The estimated likelihood of an attack is the conditional probability of each of the three events, as shown by the Bayes Theorem.11 Figure 6 illustrates this simplified system. Based on a study conducted by Barkly Research, the probabilities used in figure 6 represent the risk in a real system.12
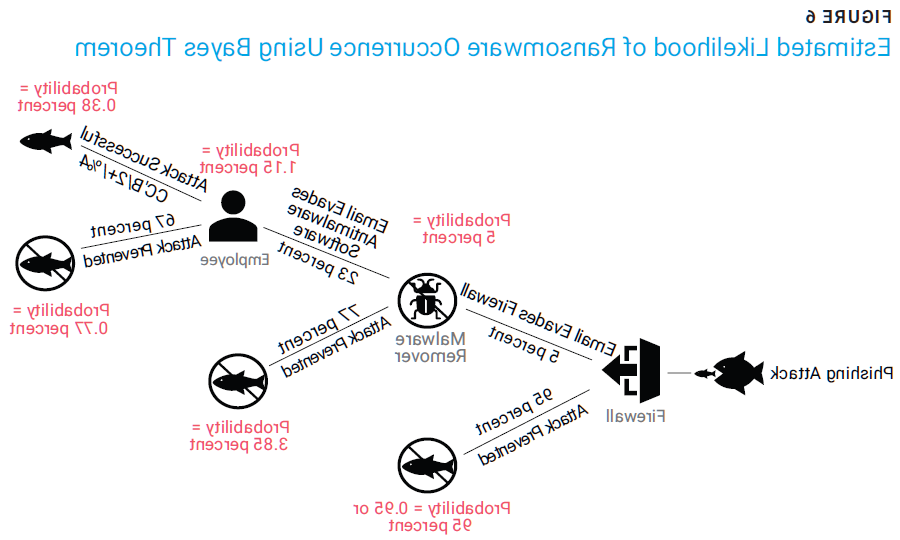
Figure 6 shows that the estimated likelihood of a ransomware phishing attack being successful is 0.38 percent for each attack launched on the system. This is determined by estimating the probability of each event that happens along the path. Figure 7 shows the probabilities to further illustrate the concept.13

If the effectiveness of the firewall is 95 percent, then that means it blocks 95 percent of the attacks, but 5 percent of threats make it to the next step. The malware removal software is estimated to be 77 percent effective; however, only 5 percent of the threats will be evaluated by the antimalware software because 95 percent of the threats were already removed by the firewall. The result is 3.85 percent (5 percent of 77 percent) of the threats will be removed and 7.75 percent (5 percent of 23 percent) will not be removed. Combined, the firewall and the antimalware software allow only 1.15 percent of the threats to get to an employee. This analysis assumes that the employee identifies such attacks and takes appropriate action 67 percent of the time. The outcome is that 0.77 percent of the threats are removed (1.15 percent of 0.67 percent) and 0.38 percent (1.15 percent of 0.33 percent) are not removed. The overall probability of the system failing is the product of all three individual components failing.
A risk-first approach allows IT managers to focus specifically on each type of attack and the possible associated attributes.
The Bayes Theorem provides a systematic approach for developing a more realistic estimate of the current risk of a system. This example shows the result of estimating the probability that one ransomware attack will be successful based on the current system components. Each organization should develop a Bayes model of its system and determine the probability of each type of attack.
Step 5: Estimating an Organization’s Annual Total Expected Cost
The annual total expected cost of information security attacks is the combined cost of occurrences, the probability of these occurrences and the types of attacks that are most likely for the organization. A risk-first approach allows IT managers to focus specifically on each type of attack and the possible associated attributes. Figure 8 shows the average reported data for four major types of information security attacks for organizations.14
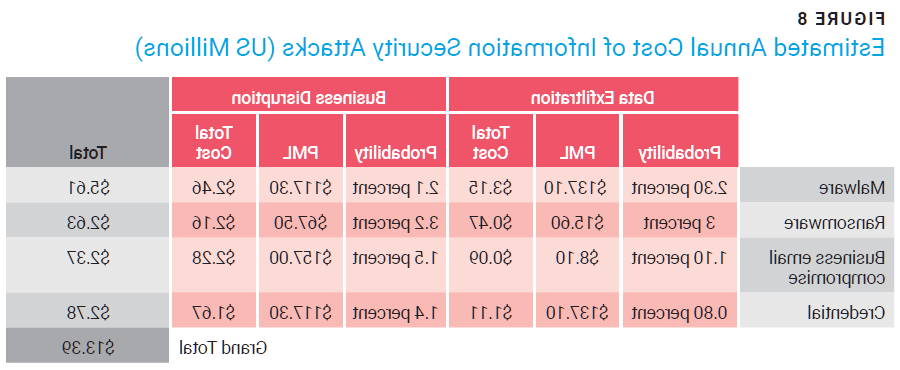
The data in figure 8 show a more complete picture of the risk associated with information security attacks. Two categories that have become more important in recent years are business email compromises (BEC) and credential compromises. These attacks are focused on members of the organization who have increased access to data or the ability to transfer funds. Credential compromises often affect the same business components as malware, so the probable maximum loss for these attacks is usually the same as for malware attacks. However, business email compromises have much greater costs associated with business disruptions than with data exfiltration. By taking the time to create a similar table, IT managers can create a baseline of the risk the organization is accepting with the current budget.
Creating a Risk-First Information Security Budget
These steps to implementing a risk-first approach help the IT manager gain a greater understanding of the financial risk associated with the current budget. There may be no need to change the budget if the risk is acceptable. However, that is unlikely, and a revised budget is usually needed to manage organizational risk.
For the current scenario, figure 8 shows that the organization could incur the greatest loss from data exfiltration due to a malware attack (US$3.16 million). The IT manager could reduce this risk by making changes to the information security system that would reduce either the current probability of an attack (2.3 percent) or the possible maximum loss (PML) (US $137.1 million).
The Bayes Theorem can be used to identify ways to reduce the overall probability of an occurrence. Since the overall probability results from the combination of all events, the likelihood of an attack can be decreased by increasing the effectiveness of current components, by replacing components with more effective components, or by adding components.
Adding a more effective firewall could reduce the probability of a malware attack, given that the probability of the system failing is the product of each system failing. Replacing a firewall with one that is more effective could create a positive return on investment if the new firewall costs less than the risk associated with the current firewall. In the current example, what happens when an organization replaces the existing firewall (95 percent effective) with a firewall that is 97.5 percent effective?
- A firewall that is 95 percent effective has a 5 percent failure rate.
- A firewall that is 97.5 percent effective has a 2.5 percent failure rate.
The original firewall allows twice as many threats to get past than the more effective one. This doubles the overall probability of an information security attack being successful. Replacing the firewall could reduce the costs associated with a malware attack by US$2.81 million (US$5.62 ÷ 2).
Similar arguments can be made for increasing awareness training for employees, especially for those employees who are more likely to be targeted for business email and credential compromises. Security awareness is the knowledge and attitude instilled in employees regarding the protection of the physical and, especially, the information assets of the organization.15 The risk-first approach allows IT managers to calculate a potential organizational loss based on employee activities and could increase security awareness and decrease successful attacks.
A second way for IT managers to reduce the overall risk to their organizations is to find ways to reduce the cost of a security attack. One option is to mitigate the overall cost in the event an attack is successful. The Bayes Theorem can once again be applied since each situation can be defined in mutually exclusive terms. For example, having an effective system backup plan can reduce business disruption costs. Figure 9 illustrates both having a backup and not having a backup.16
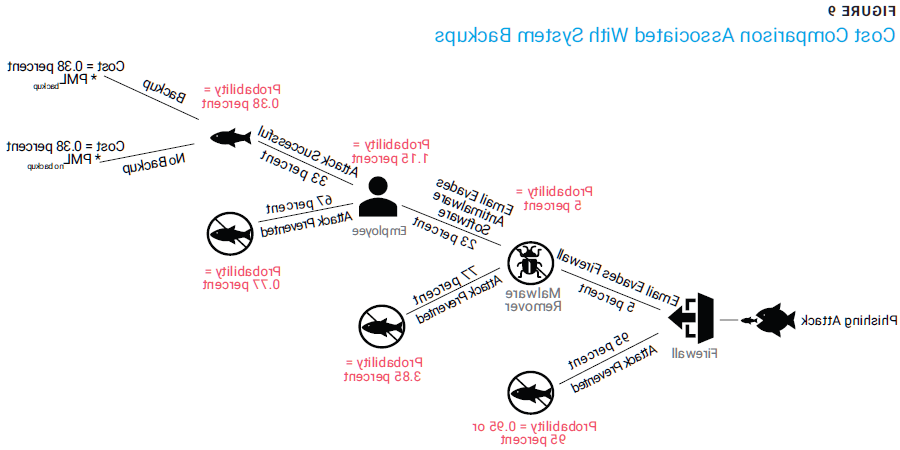
The cost associated with the risk of not having a backup now becomes more concrete since the biggest aim after an attack is to restore the system.17 A similar situation occurs when discussing whether an attack can be contained. Finding ways to lower the PML results in lowering the overall financial risk for the organization.
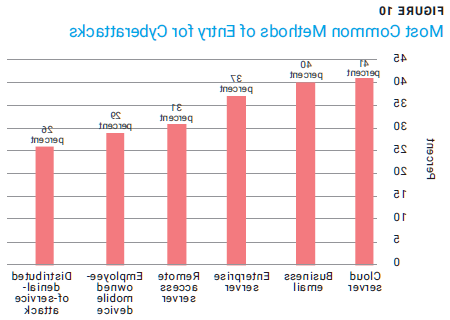
A final area of consideration is the use of policies that could reduce organizational risk. Attacks on private devices affect employees-and sometimes their organizations-because these attacks can result in compromised organizational data. Employees were the initial entry point for more than half of cyberattacks on European and US enterprises in 2022 (figure 10), with 29 percent coming from employee-owned mobile devices.18 Policies that restrict the use of private devices to access organizational data might decrease the number of successful attacks.
Conclusion
There will always be risk associated with information security because it is impossible to have completely flawless security.19 Organizations could spend all their revenue building fortresses around servers, restricting the use of every device, and stopping all email traffic to employees, yet attacks would still occur. The goal must be to determine the current risk to the organization and find ways to reduce that risk. Understanding the most likely events and their associated costs allows IT managers to focus on the largest financial risk to the organization. This allows for systematic development of priorities while developing a budget that is directed at reducing the overall risk. Taking a risk-first approach to information security therefore becomes defensible during budget discussions and can lead to competitive advantages for the organization.
Understanding the most likely events and their associated costs allows IT managers to focus on the largest financial risk to the organization.
Endnotes
1 Kshetri, N.; Cybercrime and Cybersecurity in the Global South, Palgrave Macmillan, United Kingdom, 2013
2 Purplesec, "Cyber Security Statistics: The Ultimate List of Stats, Data, and Trends for 2023," http://purplesec.us/resources/cyber-security-statistics/
3 Bernard, J.; D. Golden; M. Nicholson; "Reshaping the Cybersecurity Landscape: How Digitalization and the COVID-19 Pandemic Are Accelerating Cybersecurity at Many Large Financial Institutions," Deloitte, 24 July 2020, http://www2.deloitte.com/us/en/insights/industry/financial-services/cybersecurity-maturity-financial-institutions-cyber-risk.html
4 Ibid.
5 Sava, J.; "Spending on Cybersecurity Worldwide From 2017-2022," Statista, 28 November 2022, http://www.statista.com/statistics/991304/worldwide-cybersecurity-spending/
6 Ponemon Institute, The 2021 Cost of Phishing Study, USA, June 2021, http://www.proofpoint.com/us/resources/analyst-reports/ponemon-cost-of-phishing-study
7 Ibid.
8 Ibid.
9 Ibid.
10 Catan, I.; "The First Steps of Quantitative Risk Management," ISACA® Journal, vol. 3, 2019, http://9fsw.1acart.com/archives
11 Bayes, T.; "An Essay Towards Solving a Problem in the Doctrine of Chances," Philosophical Transactions of the Royal Society of London, vol. 53, 1763
12 Kern, C.; "Ninety-Five Percent of Ransomware Attacks Bypass Firewalls; 77 Percent Permeate Email Filtering," VarInsights, 22 November 2016, http://www.varinsights.com/doc/of-ransomware-bypass-firewalls-email-filtering-0001
13 Ibid.
14 Op cit Ponemon Institute
15 Kakareka, A.; "Detecting System Intrusions," Network and System Security, Elsevier, Netherlands, 2013
16 Op cit Kern
17 Axelrod, C.; "Cybersecurity and Critical Infrastructure: Looking Beyond the Perimeter," Information Systems Control Journal, vol. 3, 2006
18 Hiscox, The Hiscox Cyber Readiness Report 2022, Bermuda, http://www.hiscox.com/cybersecurity
19 Ghosemajumder, S.; "You Can’t Secure 100 Percent of Your Data 100 Percent of the Time," Harvard Business Review, 2017, http://hbr.org/2017/12/you-cant-secure-100-of-your-data-100-of-the-time
PETER GROSSER
Is an undergraduate student at Ludwigshafen University of Business and Society (Ludwigshafen, Germany), participating in a cooperative study program with SAP SE, a leading enterprise software company. He has gained practical experience through internships across multiple security departments, including security operation centers. His research interests include the realm of enterprise security strategies and operations.
GERALD F. BURCH | PH.D.
Is an assistant professor at the University of West Florida (Pensacola, Florida, USA). He teaches courses in information systems and business analytics at both the graduate and undergraduate levels. His research has been published in the ISACA® Journal and several other peer-reviewed journals. He can be reached at gburch@uwf.edu.
